CVE-2023-22527
Atlassian Confluence Remote Code Excecution Vulnerability

DESCRIPTION
CVE-2023-22527 is a remote code execution (RCE) vulnerability affecting Atlassian Confluence Data Center and Confluence Server. Atlassian, the software developer behind Confluence, disclosed this security flaw on January 16, 2024.
Technically, the vulnerability involves Object-Graph Navigation Language (OGNL) injection. OGNL is an expression language used in Java-based software development. In this context, the vulnerability allows unauthenticated attackers to inject and execute remote code on vulnerable Confluence instances. Successful exploitation could result in unauthorized system access, data manipulation, and potentially full takeover of the compromised system.
Severity Level: Critical (10.0): Atlassian rates the severity level of this vulnerability as critical, given the maximum score of 10.0 on the Common Vulnerability Scoring System (CVSS). The high severity level indicates that this vulnerability has the potential for serious security impact.
CVSS Vector (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H)
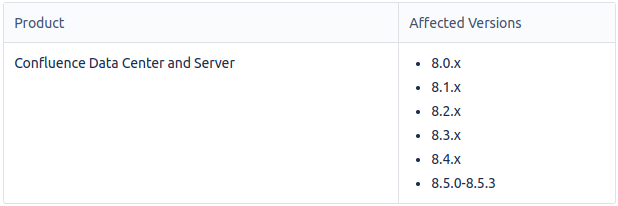
AFFECTED SYSTEMS
VULNERABILITY IMPACT
The CVE-2023-22527 vulnerability has serious implications as it can be exploited for remote code execution (RCE) on the Atlassian Confluence Data Center and Confluence Server platforms. The impact of exploiting this vulnerability involves the potential for unauthorized access to vulnerable Confluence systems and can lead to various negative consequences, including:
• Unauthorized Access: Attackers who successfully exploit this vulnerability can gain unauthorized access to the affected Confluence system. This may include access to sensitive data, user information, and system configurations.
• Arbitrary Code Execution: With remote code execution, attackers can execute arbitrary commands or scripts on the compromised system. This can be used to perform various malicious actions, including deleting or corrupting data, stealing sensitive information, or even taking full control of the system.
• Data Manipulation: Exploiting this vulnerability can allow attackers to manipulate the data stored within the Confluence platform. This could involve altering information, deleting data, or inserting false data.
It's important to remember that promptly updating the Confluence software to the patched version is a crucial step in mitigating the risk of exploiting this vulnerability. Additionally, affected organizations should conduct additional security evaluations and monitoring to ensure that there are no signs of exploitation or compromised data.
RECOMMENDATIONS
• Update to the Latest Version: Atlassian recommends Confluence users affected by the vulnerability to promptly update their software to the latest patched version. The patched versions include Confluence Data Center and Server versions 8.5.4 (LTS) or 8.5.5 (LTS), as well as Confluence Data Center versions 8.6.0, 8.7.1, and 8.7.2.
• Update Affected Installations: If you are using a Confluence version listed in the affected versions list (such as versions 8.0.x to 8.5.3), it's essential to update to the patched version immediately.
• No Known Workaround (Mitigation): Unfortunately, there are no known workarounds to address this vulnerability. Updating to the latest version is the only recommended way to remediate the vulnerability.
Taking these preventive measures is crucial to protect systems and data from potential exploitation and negative impacts that may result from CVE-2023-22527 vulnerability.