CVE-2023-34048
VMware vCenter Server contains an out-of-bounds write vulnerability

DESCRIPTION
CVE-2023-34048 is the assigned number to detail a security vulnerability found in VMware vCenter Server. It is an out-of-bounds write-based vulnerability discovered in the DCERPC (Distributed Computing Environment/Remote Procedure Call) protocol implementation used by vCenter Server. This vulnerability has a very high severity level with a CVSS (Common Vulnerability Scoring System) base score of 9.8, indicating a critical vulnerability.
The vulnerability explains that through the network, a malicious actor with access to the vCenter Server can trigger an out-of-bounds write that could potentially lead to remote code execution. In other words, a successful attack through this vulnerability could allow an attacker to execute malicious code on the affected system.
This vulnerability poses a serious threat to the security of systems running VMware vCenter Server, and it is important to promptly apply the updates released by VMware to protect systems from potential exploitation by attackers. Due to its serious potential impact, this vulnerability has a high score on the CVSS severity scale, which is 9.8.
AFFECTED SYSTEMS
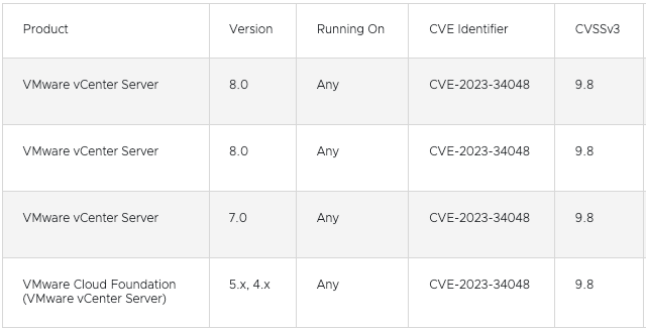
The CVE-2023-34048 vulnerability affects VMware products, namely VMware vCenter Server and VMware Cloud Foundation. Therefore, systems running these products may be affected by the vulnerability. Here is a list of impacted products:
VULNERABILITY IMPACT
The impact of CVE-2023-34048 vulnerability is very serious and includes:
• Remote Code Execution: Attackers who successfully exploit this vulnerability can execute malicious code on the affected system. This means that attackers can take control of VMware vCenter servers remotely.
• System Damage: Attackers can damage the system or cause significant disruptions in server operations. This can disrupt organizational operations, lead to downtime, and result in serious data loss.
• Potential Unauthorized Data Access: Attackers can access and steal data stored on the affected system. This includes sensitive and confidential data that can threaten the privacy and security of the organization.
• Server Ownership: Attackers who successfully exploit this vulnerability can take over control of the server, which can be used for further malicious activities or as a means to launch attacks on broader networks.
RECOMMENDATIONS
General recommendations to address CVE-2023-34048 vulnerability are as follows:
• Software Updates: Apply security updates released by VMware. These updates are the primary solution to address this vulnerability. Make sure to follow the update guidelines and procedures provided by VMware.
• Patch Monitoring: In addition to updates for CVE-2023-34048, ensure that all other security patches have also been applied to your systems. System security should always be regularly updated.
• Removal of Workarounds: If you have previously implemented temporary workarounds to address previous vulnerabilities, make sure to remove these workarounds after applying security updates. Workarounds may no longer be necessary and can affect system performance or functionality.