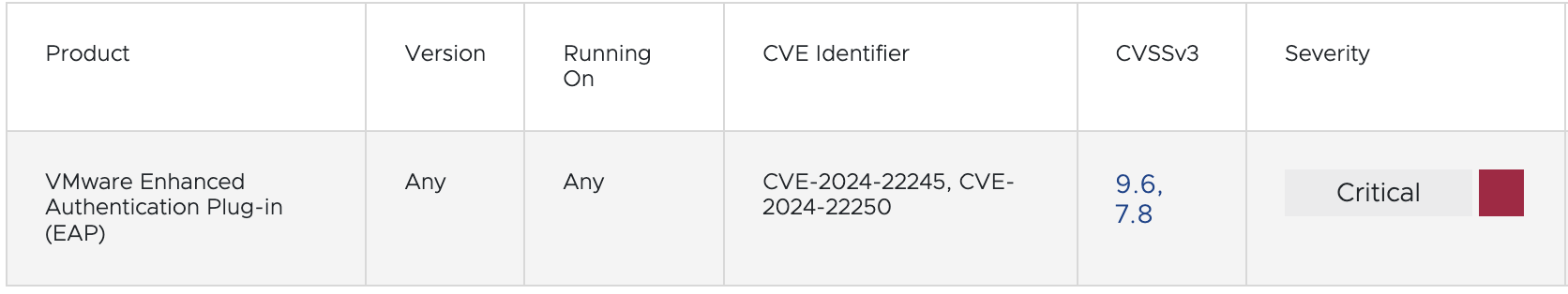
CVE-2024-22250
Session Hijack Vulnerability in Deprecated EAP Browser Plugin

DESCRIPTION
CVE-2024-22250 is a security vulnerability found in the deprecated VMware Enhanced Authentication Plug-in (EAP) browser plugin. This vulnerability is identified as a Session Hijack vulnerability, allowing an attacker with unprivileged local access to a Windows operating system to hijack EAP sessions issued by domain users with privileges on the same system.
Session Hijack vulnerability in Deprecated VMware Enhanced Authentication Plug-in could allow a malicious actor with unprivileged local access to a windows operating system can hijack a privileged EAP session when initiated by a privileged domain user on the same system.
CVE-2024-22250 is a critical vulnerability with a CVSS score of 7.8 that allows malicious actors with unprivileged local access to Windows systems to hijack privileged EAP sessions. While there are currently no known proof-of-concept exploits in the wild, administrators should remove the VMware EAP plugin and service to mitigate the risk. This vulnerability could potentially impact other third-party vendors or technologies that rely on VMware EAP for authentication.
Severity of CVE-2024-22250 is "HIGH" with Base Score: 7.8
CVSS Vector: CVSS:3.1/AV:L/AC:H/PR:L/UI:N/S:C/C:H/I:H/A:H
AFFECTED SYSTEMS
The systems affected by CVE-2024-22250 are:
Affected Versions:
• Systems running VMware Enhanced Authentication Plug-in (EAP) version 6.7.0.
• Systems using VMware Plugin Service to support EAP.
Although EAP has been discontinued since 2021, this vulnerability may still impact systems running the affected plugin version. Therefore, users or organizations still using or relying on the plugin should take immediate mitigation actions recommended by VMware to protect their systems from CVE-2024-22250 exploitation.
VULNERABILITY IMPACT
Authentication Abuse and Session Hijacking:
Attackers can exploit this vulnerability to abuse authentication by hijacking secure authentication sessions from affected EAP users. This could lead to unauthorized access to user accounts and control over the authentication session.
Hijacking of Secure EAP Sessions:
In an attack scenario, attackers can manipulate target domain users with EAP installed in their web browsers. Thus, attackers can request and relay service tickets for arbitrary Active Directory (AD) Principal Names (SPNs), hijack secure EAP sessions, and gain unauthorized access.
Potential Full Control over VMware Environment:
Exploiting CVE-2024-22245 can grant attackers full control over administrator accounts in the VMware environment. This could result in significant security and data integrity losses stored and managed in the VMware environment.
RECOMMENDATIONS
Uninstall Plugin:
VMware recommends completely removing the "VMware Enhanced Authentication Plug-in 6.7.0" browser plugin. This can be done by manually removing the plugin from the affected web browser.
Disable Service:
In addition to removing the plugin, VMware also recommends permanently disabling the "VMware Plug-in Service" supporting service. This can be done through service management on the affected operating system.
Use PowerShell:
If complete removal is not feasible immediately, VMware also recommends using PowerShell commands to temporarily disable the affected service. This can be done temporarily as a temporary mitigation while awaiting complete plugin removal.
These steps are necessary to reduce the risk of CVE-2024-22250 exploitation, which could lead to unauthorized access and hijacking of secure authentication sessions. By removing the plugin and disabling the affected service, systems will be better protected from potential attacks exploiting this vulnerability.