CVE-2024-3400
Zero-Day Remote Code Execution Vulnerability in GlobalProtect

DESCRIPTION
CVE-2024-3400 is a security vulnerability that allows unauthenticated attackers to execute arbitrary code with root privileges on firewalls running the GlobalProtect feature of Palo Alto Networks' PAN-OS software. This vulnerability occurs due to a command injection vulnerability in the GlobalProtect feature.
This is a serious vulnerability that requires immediate action from network administrators to update their firewall software with the latest patches released by Palo Alto Networks. It is essential to prevent exploitation of the vulnerability by potential attackers, which could result in system damage and significant losses for affected organizations.
The vulnerability is classified as Zero-Day, meaning it was exploited before the vendor became aware of it or released a patch to fix it. This vulnerability has a very high severity level, rated as "CRITICAL," with a CVSSv4.0 base score of 10, indicating a highly dangerous potential for attacks.
CVSSv4.0 Base Score: 10
(CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:N/VC:H/VI:H/VA:H/SC:H/SI:H/SA:H/AU:Y/R:U/V:C/RE:M/U:Red)
AFFECTED SYSTEMS
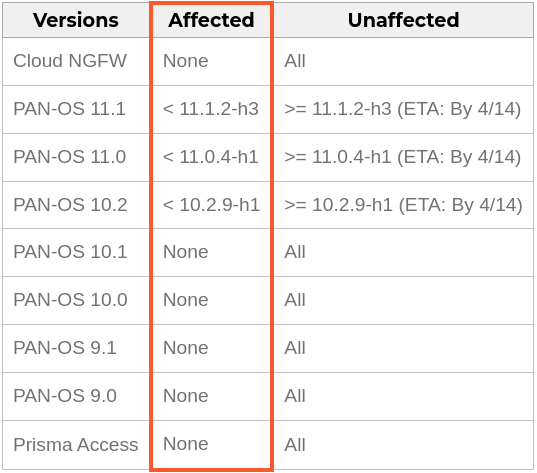
Systems affected by CVE-2024-3400 are firewalls running Palo Alto Networks' PAN-OS software. Specifically, this vulnerability affects firewalls configured with the GlobalProtect feature. Vulnerable software versions include PAN-OS 10.2, 11.0, and 11.1.
VULNERABILITY IMPACT
• Arbitrary Code Execution:
AThis vulnerability allows unauthenticated attackers to execute uncontrolled code on the affected firewall. By exploiting this vulnerability, attackers can execute any code with root privileges on the device, which can be used to perform various malicious actions, such as modifying firewall configurations, accessing or damaging sensitive data, or even deleting or stopping firewall operations altogether.
• Potential Influence:
This vulnerability affects firewalls running specific versions of Palo Alto Networks' PAN-OS software and configured with the GlobalProtect feature. Consequently, organizations using firewalls with this configuration could suffer serious consequences if this vulnerability is exploited by attackers, including significant data loss, decreased productivity, or even leakage of sensitive information.
RECOMMENDATIONS
CVE-2024-3400 is a critical vulnerability with a CVSS score of 10.0, occurring in the form of command injection in the GlobalProtect feature. With this vulnerability, an unauthenticated attacker can exploit it to execute arbitrary code with root privileges on the firewall.
To address this vulnerability, Palo Alto Networks has released software updates in the following versions:
• PAN-OS 10.2.9-h1
• PAN-OS 11.0.4-h1
• PAN-OS 11.1.2-h3
Patches for other commonly used maintenance releases are expected to be released in the coming days. This means that Palo Alto Networks will release additional software updates for other PAN-OS versions commonly used in production environments.
This step aims to ensure that all users of PAN-OS affected by CVE-2024-3400 can promptly update their software and reduce the risk of exploitation of this vulnerability.